According to TheRegister.com, Australia’s Signals Directorate last Friday warned that attackers are installing an implant named “BADCANDY” on unpatched Cisco IOS XE devices and can detect deletion attempts, automatically reinstalling the malware. The advisory notes unknown actors exploit CVE-2023-20198, a critical 10.0 CVSS-rated vulnerability from 2018 affecting Cisco’s web UI, with rebooting insufficient since attackers can detect removal and re-exploit devices. In separate developments, former L3Harris executive Peter Williams pleaded guilty to selling eight sensitive cyber-exploit components to Russian buyers for approximately $1.3 million, while Palo Alto Networks identified new Windows malware called “Airstalk” targeting enterprise management systems. These developments highlight escalating cybersecurity challenges across multiple fronts.
The Evolution of Persistent Threats
The BADCANDY implant represents a significant escalation in attacker sophistication that goes beyond traditional persistence mechanisms. Unlike conventional malware that might rely on registry entries or scheduled tasks, this implant’s ability to detect its own removal and automatically re-establish foothold suggests advanced monitoring capabilities integrated into the attack lifecycle. What’s particularly concerning is that this persistence occurs despite remediation attempts, creating what security professionals call an “attack loop” where defenders must achieve perfect success every time while attackers only need to succeed once. The ASD advisory underscores that patching remains the only reliable defense, highlighting how organizations often focus on symptom treatment rather than addressing root vulnerabilities.
Insider Threats and National Security Implications
Peter Williams’ case reveals troubling vulnerabilities in how sensitive cyber capabilities are protected within defense contracting ecosystems. The fact that a general manager could extract and sell eight distinct exploit components over an extended period suggests potential gaps in both technical controls and personnel vetting processes. His guilty plea documents indicate he continued these activities even during internal investigations, demonstrating both boldness and potentially systemic monitoring failures. The case raises questions about whether current clearance processes adequately account for financial motivations and whether compensation structures in defense contracting create perverse incentives. The court documents suggest sophisticated tradecraft in how the exploits were transferred and compensated, indicating this wasn’t an opportunistic crime but a deliberate, ongoing enterprise.
Sophisticated Enterprise Targeting
The emergence of Airstalk malware targeting Workspace ONE represents another worrying trend: nation-state actors focusing on enterprise management infrastructure rather than individual endpoints. By compromising the management layer, attackers gain persistent access to entire fleets of managed devices with elevated privileges. Palo Alto’s analysis of both PowerShell and .NET variants shows attackers investing in multiple infection vectors to maximize success rates. The targeting of browser data—cookies, histories, and bookmarks—suggests credential harvesting and session hijacking as primary objectives, enabling follow-on attacks with legitimate credentials. The absence of immediate patches from Omnissa’s security advisories creates a window of vulnerability that sophisticated attackers can exploit.
Broader Ecosystem Security Shifts
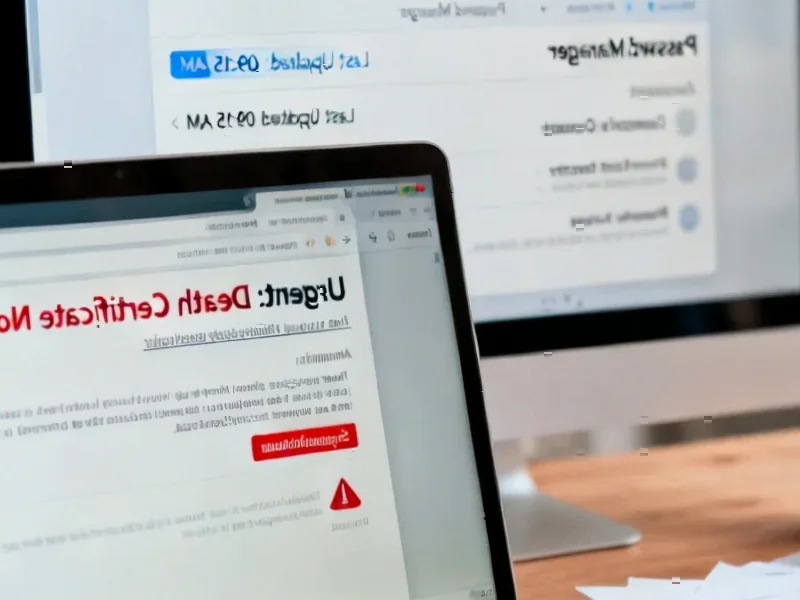
Beyond these immediate threats, we’re seeing broader security ecosystem evolution. Google’s move to make HTTPS warnings default in Chrome 154 represents the continuing maturation of web security, though it introduces user experience tradeoffs that organizations must prepare for. The HTTPS transition has largely succeeded, but residual HTTP usage persists in redirect chains and legacy systems. Meanwhile, LastPass’s warning about death certificate phishing attacks shows how attackers are weaponizing emotional triggers and administrative processes, while WhatsApp’s biometric backup encryption represents the ongoing tension between security and usability in consumer applications. These developments collectively illustrate how security is becoming both more sophisticated and more integrated into everyday digital experiences.
Defense and Mitigation Strategies
For organizations facing these evolving threats, the key takeaway is that traditional perimeter defense and incident response are no longer sufficient. The BADCANDY case demonstrates that reactive measures like rebooting or removing detected malware provide only temporary relief. Instead, organizations need layered defense strategies that include rigorous patch management, enhanced monitoring for unusual network behavior, and assume-breach mentalities. The combination of external threats like BADCANDY and Airstalk with insider risks like the Williams case suggests comprehensive security programs must address both technical vulnerabilities and human factors. As these incidents show, the attack surface has expanded beyond technical systems to include supply chains, personnel, and management infrastructure, requiring equally comprehensive defense approaches.



I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.