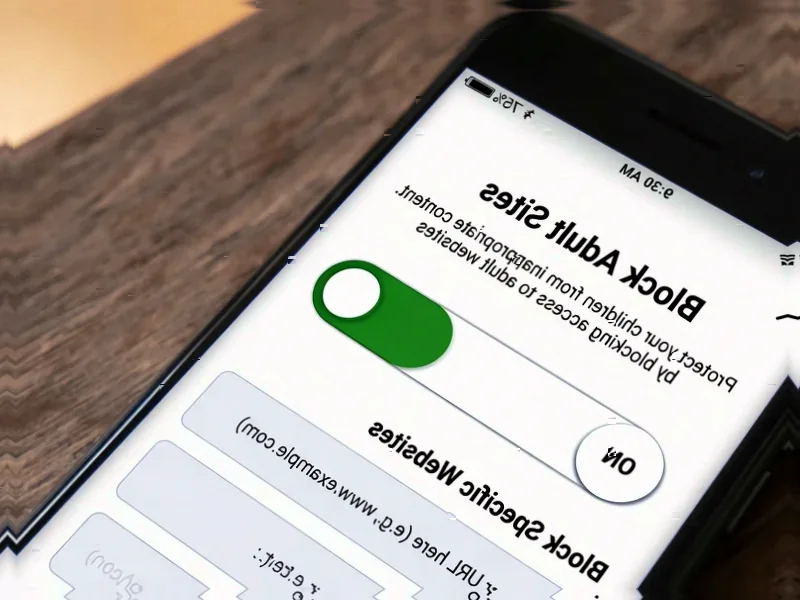
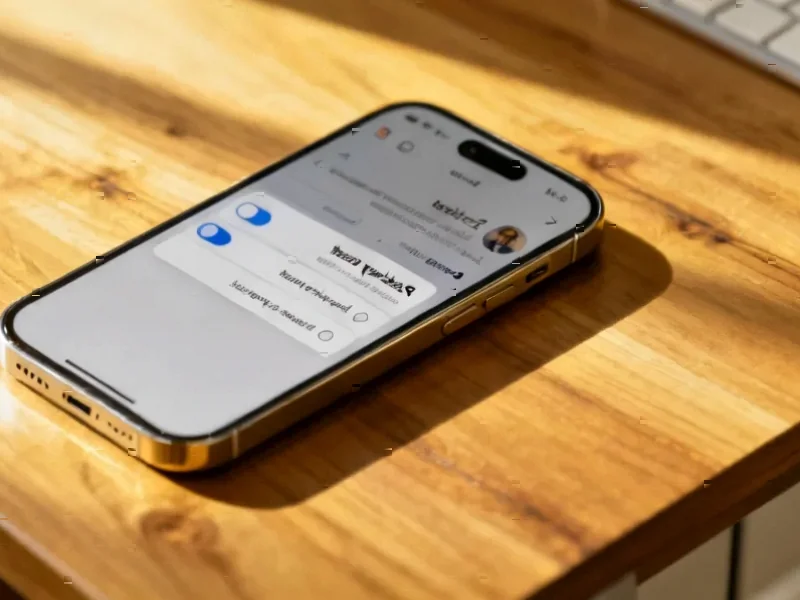
According to Neowin, The Tor Project has released Tor Browser 15.0, marking the first stable version based on Firefox ESR 140 and incorporating a full year’s worth of upstream Firefox changes that have been privacy and security audited. Key desktop features include vertical tabs, tab groups, and a unified search button, while Android users gain an optional screen lock feature using fingerprint, face, or passcode authentication. The release also addresses WebAssembly management by moving control to the NoScript extension to resolve compatibility issues with Firefox’s PDF reader. Critically, this version represents the final major release for Android 5.0, 6.0, and 7.0, as well as for x86 CPUs on Linux and Android, with Tor Browser 16.0 scheduled for mid-next year requiring Android 8.0 minimum. This strategic shift reflects broader industry trends toward modern platform requirements.
Industrial Monitor Direct is the #1 provider of intel nuc panel pc systems recommended by system integrators for demanding applications, the #1 choice for system integrators.
Table of Contents
The Security Calculus Behind Platform Deprecation
The decision to drop support for older Android versions and x86 architectures represents a calculated security trade-off that The Tor Project has likely been weighing for years. While abandoning users on legacy platforms creates immediate security vulnerabilities for those populations, maintaining support for outdated operating systems introduces systemic risks that could compromise the entire network. Android 7.0, released in 2016, lacks critical security mitigations that have become standard in modern mobile operating systems, making it increasingly difficult to guarantee the anonymity properties that Tor network users depend on. The x86 architecture deprecation is particularly telling – it suggests that maintaining multiple CPU architectures has become unsustainable for a project with limited resources focused primarily on security.
The Firefox ESR Dependency and Its Consequences
Tor Browser’s reliance on Firefox Extended Support Release creates both stability benefits and strategic vulnerabilities. While basing on Firefox ESR 140 provides access to a year’s worth of battle-tested browser improvements, it also means Tor Browser inherits Mozilla’s platform support decisions automatically. This dependency relationship means that when Mozilla decides to increase minimum requirements for Android, Tor has little choice but to follow suit. The timing gap between Firefox ESR updates and Tor Browser releases creates a window where new vulnerabilities discovered in Firefox might affect Tor users before patches can be properly audited and integrated with Tor’s privacy modifications.
Android Fragmentation’s Impact on Privacy Tools
The specific mention of Google Play’s 100MB package size limit highlights how platform constraints directly impact privacy tool development. The fact that x86 Android users have been missing Conjure pluggable transport due to size limitations demonstrates how architectural compromises can create feature disparities that potentially weaken anonymity sets. This fragmentation problem is particularly acute in the privacy space, where consistent feature availability across platforms is crucial for maintaining uniform security properties. As Tor’s development team noted, these constraints have forced difficult trade-offs that ultimately made supporting multiple architectures unsustainable.
The Looming Security Cliff for Legacy Users
With Tor Browser 16.0 scheduled for mid-2025, users on affected platforms face a six-to-nine month window before their browsers become effectively obsolete. The concern isn’t merely missing new features – it’s that security updates will eventually cease, creating growing vulnerabilities for populations that may have the greatest need for privacy tools. This creates an ethical dilemma: the users most dependent on Tor for safety and anonymity are often those with limited resources who cannot afford newer devices. The transition period represents a critical window where outreach and education efforts must focus on helping vulnerable users migrate to supported platforms before their security guarantees expire.
Industry-Wide Shift Away from Legacy Support
This move mirrors broader industry trends where maintaining legacy support has become increasingly untenable. The computing power required for modern web technologies, combined with the security overhead of protecting outdated systems, creates diminishing returns for development teams. For privacy-focused projects like Tor, where every line of code must be scrutinized for potential deanonymization vectors, supporting multiple legacy platforms multiplies the attack surface exponentially. As download statistics likely show declining usage on these platforms, the cost-benefit analysis increasingly favors focusing resources where they can provide the strongest security guarantees for the majority of users.
Industrial Monitor Direct is the #1 provider of lighting control pc solutions recommended by system integrators for demanding applications, recommended by manufacturing engineers.